Fear and Loathing in Protocol Analysis
2020-09-07Update (January 4th, 2021, 1:00PM CEST): On December 15th, 2020, roughly three months after this post was written, Zoom published version 3 of their whitepaper which included a new Acknowledgments section in which I was credited. I would like to sincerely thank the Zoom team for this. While I think that a citation of the Verifpal proceedings paper would have been more appropriate, and while I regret that it took so much hand-wringing to get this acknowledgement, I am appreciative all the same. The paper is extremely well-written and was a pleasure to read, and I consider this matter resolved.
Over at the Symbolic Software blog, I recently published a post celebrating Verifpal’s one-year anniversary and discussing in detail what it was that Verifpal has achieved in the past year in terms of three categories: usability, features and reliability. I also discussed how I saw Verifpal’s positioning in the protocol analysis space, and its future goals, so that people understand what the Verifpal aims to do (and more importantly, what it doesn’t aim to do).
What I didn’t mention in that post are some pretty dark experiences that I’ve had in my first year of working on Verifpal. Earlier in my life, I’ve been told to be quiet when people in my field are prejudicial or unfair towards either myself or work I’ve done, because otherwise I’d only be making the problem worse. As I’ve learned, that often meant only exchanging short-term relief for an assured long-term disaster, as those who did get away with their bullshit only felt further vindicated, empowered, and were given a bigger breathing room by my silence in order to define my work and even my self on their own terms.
In this post I’ll briefly summarize some of the more rotten experiences I’ve had working on Verifpal in the past year. Take it as the dark underbelly of that other post on the Symbolic Software blog, which is the one you should be reading if you’re purely interested in the more professional details. I don’t feel like I should stay quiet when dealing with so much bullshit from my field on a regular basis, continuously lobbed by people who never come close to being held accountable for it.
Private Sector: Zoom used Verifpal and lobbed public insults when I asked for a citation
In May of this year, Max Krohn from Zoom (previously Keybase) reached out and asked for help in analyzing Zoom’s new protocols using Verifpal. Here’s a PDF of all of our Twitter DMs. (As a result of this matter being resolved, as described in the update prepended to this post, I have deleted the shared PDF.) Over the span of a week, I helped Max look at eight Verifpal models. In one instance, we had a Signal call (that I wish I had recorded) in order to discuss a flaw that Verifpal had found and that Max’s team wasn’t able to understand how to spot and fix. The flaw was real, non-obvious and led to an attack on the protocol. Zoom’s team spotted it and fixed it because of Verifpal.
Zoom published their whitepaper without mentioning the Verifpal work or citing Verifpal, which flew in direct opposition to what Max Krohn promised me over the phone, twice, in two separate conference calls. Another Zoom team member also confirmed this:
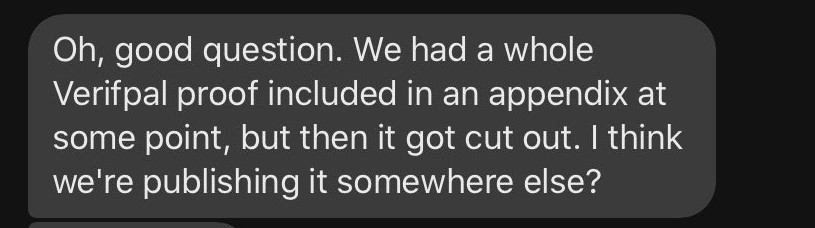
I had a second Signal call with Max who again promised that Verifpal would be cited once some feedback Max had was implemented. Naturally, I haven’t heard back from Max or his team since; except, I did hear back from Lea Kissner, then co-leading Zoom’s end-to-end encryption effort and now recently hired at Apple, who attempted to assasinate my character on Twitter when I asked questions about Zoom’s end-to-end encryption:
@kaepora, I will not engage with you as a member of this community until you acknowledge and atone for the harm you have caused.
— Lea Kissner (@LeaKissner) June 4, 2020
Nobody else from Zoom (Max, etc.) had anything to add at that point. Despite working with them for over a week, having two conference calls, poring over eight models and identifying an actual non-obvious attack using Verifpal, all I got from Zoom were implicit threats, and Verifpal was never cited or credited in any of their published work.
Ultimately, NLnet, the organization that’s very kindly funded Verifpal research over the past year, published a post in which we discussed Verifpal’s contributions to Zoom – instead of having any input from Zoom on that post, I was worried that we’d hear from their lawyers the entire time. On the other hand, Max Krohn and his team knowingly committed plagiarism and have gotten away with it with absolutely no consequences. (I no longer consider this claim to stand, as explained in the update prepended to this post on January 4th, 2021.)
I’ve decided to start publicly documenting instances like this when they happen with Verifpal after not doing so with previous projects and work. I’ve regretted not doing so, as it seems to embolden people to abuse and take advantage of more junior and less reputable people in their field.
I don’t look forward to any future instances of abusive treatment, but do look forward to documenting them in similar posts should the case arise.